
Corrupted smart factories
In reality, hackers haven’t waited around and it has been a while since they are trying to breach in the supposedly most secure facilities such as Nuclear Plant. Some of them have been successful.
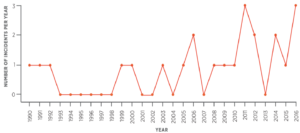
Frequency of cyber-incident at Nuclear Facilities
Nuclear and energy facilities are supposed to be the most secure factories because of the risk they present for the life of citizens. Yet, many of them were hacked or hijacked in the past years.
Power Plant infected by Malware from a consultant’s PC
The Davis-Besse nuclear power plant in Ohio (USA) was infected with the Slammer worm-along with 75,000 servers worldwide within 10 minutes of its release in 2003-after a consultant connected to the plant’s corporate network. The worm did not carry a malicious payload; rather, it overwhelmed the server by scanning random IP addresses in search of new hosts in which to propagate.
Because the corporate network was connected to the plant process control system without any type of firewall, the worm was able to jump onto plant systems and take up huge amounts of bandwidth. This shut down the safety parameter display system (SPDS) for nearly five hours, and prevented operators from seeing sensitive information about the reactor core. Fortunately, the plant was not running-however, had it been operating, this malfunction could have caused a serious problem.
Iranian facility infected by nation-state hacker
The United States and Israel are reported to have jointly developed the Stuxnet virus, which was deployed in two stages and destroyed nearly 1,000 of Iran’s 9,000 IR-1-type gas centrifuges. The first stage, reportedly released as early as 2005, was active between 2007 and 2009. This version targeted Siemens programmable logic controllers (PLCs) at the Iranian Natanz uranium-enrichment facility and attempted to disrupt uranium enrichment by closing the valves that fed uranium hexafluoride gas into the centrifuges. This version of Stuxnet ceased operation in July 2009.
The second version of the Stuxnet virus was reportedly released into Natanz in June 2009 and was revealed in 2010. This version attempted to disrupt uranium enrichment by altering the rotational speed of the gas centrifuges at Natanz. It is likely that this version of Stuxnet was introduced to a computer at the Iranian Natanz uranium enrichment facility through a USB stick, demonstrating that even facilities disconnected from the Internet are vulnerable to attack.
Korean Nuclear plant infected by Anti-Nuclear Hacktivists
Korea Hydro and Nuclear Power Co., which operates 23 of South Korea’s nuclear reactors, was hacked in December 2014. The hackers, claiming to be an anti-nuclear group based in Hawaii, used phishing e-mails to introduce malware into the commercial network. They then were able to steal the blueprints and manuals for two nuclear power plants, believed to be the Gori and Wolseong plants in South Korea. The hackers also obtained radiation-exposure estimates for surrounding areas, personal data for 10,000 employees, and electricity flow charts. These data were leaked via Twitter, and the hackers threatened « destruction » if Korea Hydro and Nuclear Power Co. did not shut down three reactors.
Isolated German Nuclear Plant infected by a malware
In April 2016, reports surfaced that the Gundremmingen Nuclear Power Plant in Bavaria was infected with malware. The discovery was made in the plant’s B unit, in a computer system that had been retrofitted in 2008 with data-visualization software accompanying equipment for moving nuclear fuel rods. Viruses have also infected 18 removable data drives associated with computers not connected to the plant’s operating systems. There was no apparent damage.
Two of the viruses found on the plant’s fuel rod– monitoring system and on the removable data drives were W32.Ramnit and Conficker. W32.Ramnit targets Microsoft Windows software systems and is designed to steal files and allow an attacker to remotely control a system that is connected to the Internet. It is often spread using removable data sticks. Conficker, which can spread through networks and jump onto removable data drives, was designed to obtain login information and financial data.
The station’s operator stated that the viruses “appear not to have posed a threat to the facility’s operations because it is isolated from the Internet.” This statement raises questions about how the “isolated” plant became infected and why the malware went undetected for so long.